Everyday, millions of workers and families sail through work or home tasks on their computers, browsing the internet, believing their anti-virus software is protecting them from all the known or unknown computer evils out there.
Nothing could be farther from the truth. Unknown to PC computer users everywhere, there are sinister dangers lurking on the internet or on software disks, dangers that your anti-virus software is not protecting you from. Worse yet, it is a well-kept industry secret, one that virus protection software companies will not warn you about. In fact, this fatal flaw is not even mentioned at anti-virus web sites.
So how can this be true in our modern enlightened world, where viruses are announced on the news as soon as they surface? How is it that anti-virus software products are singing their own praises for the Viruses, Trojans, and Worms which they claim such diligence in shielding from your computer? What else lurks out there that could damage your computer or ruin your life?
The answer is in a secret weapon perpetrated by internet marketing companies to learn all about your age, income, and buying habits. They are doing this through secret software weapons known as “parasites” that attach themselves to a host internet browser and then begin sucking details out of your personal life.
Unlike Viruses, Trojans and Worms which are intended to disrupt your computing experience, Parasites attach themselves to your computer and secretly monitor your internet surfing habits or misuse your computer for their own insidious purposes. Parasites come in all flavors. So while your firewall may protect you from dangers outside your home or office firewall, there is nothing protecting you from the stealth monitoring of parasites residing inside your computer.
Adware parasites monitor web pages you visit and rapidly search for keywords matching their own list of words that are pre-programmed to launch popup ads at you quicker than you can close them. Or, it can start launching popup or pop-under advertising windows the moment your computer establishes an internet connection.
Spyware parasites record all of your internet keystrokes and transmit them to another company, typically for marketing studies to see what products or services you view on your screen. However, spyware did not always possess these questionable tactics. Originally, internet companies used spyware to verify your identity to ensure safe communication and transactions with your computer.
Malware parasites are intended to disrupt your computer by triggering Viruses, Trojans or Worms. Or, they may take you instantly to their web site where it retrieves your user names, passwords, or financial information stored in the windows directory.
Parasites for the Savvy Surfer
You may already recognize the names of these parasites, often touted as “must haves” for the savvy surfer. Popular programs such as Internet Washer are supposed to erase your web surfing tracks so you can browse anonymously, but instead, unleash a payload of two or more parasites in your computer.
While Hotbar is supposed to speed up your web surfing, this parasite assigns a code number to your computer, then records every web page visited, every purchase made, and every keystroke entered into every form on every web page.
Ilookup is heralded as a better browser search box, but actually hijacks your home page with its own and replaces customary browser search bars with its own snoopy tools.
SpyBlast is advertised as a firewall tool for detecting intruders which it does not do, but instead, sends you popup ads.
WebHancer is supposed to enhance your web browsing experience, but instead, spies on web sites you visited. This parasite is widely distributed through music downloads from Audio Galaxy and Grokster, among others.
Not every piece of software or web site will actually rid your computer of these infections. Some of these programs claiming to rid you of unwanted pop-up ads, will end up infecting your computer with their own parasites, so be aware of Adaware. The Newbie Org web site for computer novices is apparently run by newbies themselves, as they advise troubled users to install Adaware along with other damaging software. Some web sites with good intentions such as 2-Spyware attempt to provide good advice about parasites, but have limited expertise which would have you deleting legitimate speech or monitor files that could disable some of your programs.
Infected Bargain Software
Those inexpensive CD’s priced from $5 – $10 that you see in the bargain software racks in stores, come preloaded with adware and spyware parasites which are installed on your computer along with the software program you are buying.
Hewlett-Packard’s scanning software includes an FTP program to neatly upload your photos to the internet. Intended to make uploading easy for the novice, this photo folder contains a stowaway that rides alongside your photos on their trip to the internet to track everywhere you go. Its spyware is cemented to your computer inside the “Share-to-Web” non-removable desktop icon.
These parasites can also arrive unexpectedly with the free installation disk for your new product, internet or cable purchase. Infected parasitic software have been reported coming from such well-respected companies as Amazon, Best Buy, Cannon, CorelDraw, Cosmi, Dell, DirecTV, Earthlink, Hewlett-Packard, IBM, Kensington, Logitech, MicroWarehouse, Photo Editor Software, US Robotics, Xoom, and many more. The infected parasite list even includes McAfee anti-virus protection software. How can software designed to protect your computer, end up infecting it? How does this happen?
Buying some software products from these companies may infect your computer with a popular parasite from Alset, an internet company that describes itself as “a revolutionary service that provides end-users with plain English messages to help them avoid common computer problems.”
For example, buying Cosmi’s inexpensive $10 Video Editor program containing “everything you need to make perfect movies” according to the label, also installs something you do not need – namely a parasite from Alset called Help Express. Billed as a problem solver, Help Express installs another parasite called Coupons and Offers into your print menus. So, every time you go to print, a drop down window opens and ask you if it is time to buy more ink for your printer? Then the parasite specifies the make and model number of your printer and offers to link you directly to an advertiser selling the exact type of ink used by your printer.
Trusted Software Contains Parasites
Sometimes well-respected companies with full-priced software, such as Broderbund or Mattel, engage in these sneaky practices. These companies install the Brodcast parasite and its spawn from hell into your computer when you install their software. These insidious pests drive pop-up ads to your computer like there is no tomorrow. Each time you connect to the internet, the Brodcast parasite begins rapidly firing pop-up ads at you. Most people mistakenly blame the web sites they are visiting for these annoying pop-up ads. What people do not realize is the pop-up ads are really being launched from a parasite inside their own computer which was secretly installed with their gaming, home design, home reference, or genealogy software.
Parasites Targeted at Children
While many parasites are targeted at the buying public, some innovative marketers have designed clever parasites for studying the internet browsing habits of families by targeting the youngest internet users, namely the children. One very popular parasite is a highly praised animation called Bonzi Buddy. With its animated talking parrot or purple gorilla that literally talks to your child, this internet spy is gathering information about what your child looks at on the internet. But it does not turn off its snoopy ways when the adults go online because it continues reporting their internet habits to its home base.
Another widely distributed popular parasite is Comet Cursor. This one is so popular that families seek it out and download it deliberately. With its fanciful antics, these mouse cursors enchant children while spying on their surfing habits. Of course, it does not know when an adult is browsing the internet because it continues silently spying on the browsing habits of all the family members. Another parasite aimed at children and teens is called Gator which gathers information about internet browsing and is heavily linked to all kinds of unwanted advertising and pop-up ads. However, the end result is the same – internet spying.
No Free Ride
How do otherwise intelligent shoppers, who use anti-virus software, get parasites in their computers? The answer lies in the deceptive ways in which these parasite companies will trick you, your co-workers, or members of your family, into downloading their plentiful supply of free games, free music, free software, free videos, free screen savers, and so on.
But nothing is really free on the internet. “Free” may be the gimmick that hooks you, but hidden inside the free download, is a parasite so technically superior that it secretly boards your computer and implants a two-way communication system for gathering and reporting information about you to other companies. What a high price for your family or company to pay for getting free or cheap software.
Even for families where games, videos or music are not downloaded, the marketing companies are clever enough to tempt you with free internet utility programs to improve your internet surfing experience or to block advertising or spyware. Some of these parasites even offer you free software to help you, by allegedly erasing your internet surfing tracks, or to provide you with free toolbar attachments to make surfing faster, or to supposedly block advertising or spying programs.
But what they fail to mention is their scrungy program is a ruse, a scam, a cover-up to hide their sneaky parasites hidden inside their programs. Some of these web sites will not even wait to see if you want to download the freebie with the parasite, because even if you click away from their web site, it is already too late, for your computer has already been slipped the self-installing parasite. Worse yet, most parasites will not show up in your computer’s list of startup programs or in your control panel listing software that has been added. This is deliberate to avoid detection.
But as diabolical as this seems, it gets worse. While many parasites want to know your spending habits, just as many parasites are using your internet connection to redirect pornographic traffic to web sites located in other countries.
These parasites will also use your modem to dial other countries which is why you may have found long distance calls to other countries that you did not make, but which the automatic dialing software made at your expense.
Or, if you are on a network or broadband connection, these parasites will “borrow” your company, your school, or your university’s broadband network connection to harvest their traffic and redirect potential customers to their illegal web sites.
That means while your computer is turned on and connected to the internet, these parasites will set up shop with rent-free space on your computer, making your computer the mainframe for their web page. Parasites then literally draw internet traffic to your computer to show an implanted web page while you are totally oblivious to this clandestine operation, except for occasional computer crashes or screen freezes.
A College Student’s Infected Computer
To show you how insidious these parasites are, we checked one college student’s computer. We unplugged it from the university network to see what surprises were in it. Despite the fact the student’s anti-virus software was current and operating correctly, we found his computer was infected with one Trojan virus and dozens of parasites. Prior to our checking, the student’s only complaint was his computer sometimes crashed, ran slowly, or froze up when he was typing his homework assignments. Normal typing does not require a lot of computer memory, so we suspected parasitic activity.
Fatal Attraction
We asked the student what web sites he visited and what he downloaded. He indicated a preference for gaming web sites such as Nstorm, music web sites such as Audio Galaxy and KaZaa Lite, and screen savers from many different web sites.
The student said he did not visit gambling or pornographic web sites. This was confirmed by checking the cookies, history, and temporary internet files stored on the computer.
Although the student’s computer did not contain any collection of pornographic material, we found a pornographic “home page” with active photo links and a “live” Java script located on the root drive of his computer that had been installed by a parasite. Additionally, the Windows and Program Files directories contained over a dozen self-running “online dialing” parasites for pornography, adware or spyware, including Dialer Offline (porn), Rapid Blaster (porn), Strip Player (porn), Erostars and IEAccess (installs premium rate diallers for porn sites), Gator (unwanted advertising), Online Dialer (porn), Web Dialer (porn), Dialler (porn), among others.
The student’s computer also contained the insidious Transponder Trojan which hails itself as a browser tool, but which records information entered into web page forms, such as purchases, user names, passwords, account numbers, and money transactions. Then it relentlessly transmits this information to its home server and sends back plenty of advertising. Transponder also has the malicious ability to silently install other software on your computer from its home base across the internet and was responsible for some of the auto dialing software.
We found these diabolical, self-launching parasite programs were routing internet traffic through this student’s university network connection to pornographic web sites around the world and sending him unwanted pop-up ads as well. No wonder this student complained his computer sometimes crashed, ran slowly or froze up without explanation. It was because this unwanted internet traffic was periodically overwhelming his computer. How many other universities or work places have had their network connections hijacked by pornographers?
KaZaa Lite or KaZaa Blight?
One of the world’s most popular web sites for downloadable music and videos was a hit among teens and college students as soon as it was launched. Originally a free music web site until recent changes in the law, it gleefully downloaded countless parasites into computers undetected by anti-virus software. Yet KaZaa Lite downloads so many unwanted parasites into a computer it should be named KaZaa Blight.
Why Anti-Virus Software Will Not Protect You
None of the commercial anti-virus software programs will defend your computer against an attack of parasites because they do not even detect parasites! If you want to see how diabolical this is, visit the Norton or McAfee web sites and do a word search for some of these parasites by name, and you will come up empty-handed. This is because they do not even address the problem!
The explanation given by anti-virus companies for not protecting your computer from parasites, is because parasites do not spread to other computers. Of course, this glib statement is not at all true because parasites jettison through a home or business network as quickly as a virus. The real reason anti-virus software companies are not also anti-parasites, is because many commercial web sites pay for marketing information collected by parasites. Parasites are all about making money through exploitation.
Impact of Online Banking
If you engage in online banking or stock transactions, you probably feel safe wielding deals behind a computer running anti-virus software behind a firewall and visiting secure web sites that start with “https” with the “s” representing “secure.” But what if one of these spyware parasites is recording your keystrokes from inside your computer, collecting information about your user names, passwords and account numbers? Many parasites do just that. They silently transmit this information across the ocean to unscrupulous criminals. Imagine the impact if this information about you were sold to criminals or even terrorists? How long would online banking or the stock exchange remain secure, if one day the terrorists decided to crash the United States or global world banking system, by implanting millions of home and office computers with parasites for monitoring keystrokes to bank accounts? It boggles the mind.
Your Best Defense is a Good Offense
Since most people use Microsoft Windows or Internet Explorer, parasites are written for these programs because it assures its creators of the widest possible distribution. The quickest way to avoid these parasites, even if they are already on your computer, is to simply stop using Internet Explorer and switch to a different browser. The pests will not go away, but they will sleep as long as you do not use Internet Explorer. The parasites will wake-up whenever Internet Explorer is running.
If you do not know how to switch to a different internet browser, you can overcome many of the hazards associated with Internet Explorer by turning off the Active-X and Java script functions. These features normally enable your web surfing to be filled with music, video, animation, or the ability to complete online forms for shopping or banking, for example. However, the Active-X and Javascript functions are the speedway used by parasites to race into your computer. Halting their ability to run on your computer will also prevent you from playing music, watching videos, animations or completing online forms.
Therefore, the solution is to download a less popular browser. We downloaded an older version of Netscape, the world’s second most popular browser, hoping it would be free of pests. But we were wrong. We found it came packed with a parasite when the internet radio option was selected for installation. But then, who can resist internet radio?
Even the world’s largest internet service comes with parasites. America OnLine (AOL) which bought out the previously mentioned Netscape, is used worldwide by the public and small independent businesses. Pitfalls associated with America OnLine are covered in depth in another article at this web site. Visitors to the America OnLine web site will be greeted with an option to download the latest version or Instant Messenger (IM) which allows online chats in many countries of the world. 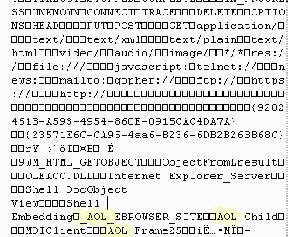 Peeking into the programming code for this parasite customized for America OnLine users, reveals its purpose is to track all web sites visited, including secure web pages for making purchases or financial transactions. Clicking on either ad for more information will inject the Alchem parasites directly into your computer which germinate into more parasites.
Peeking into the programming code for this parasite customized for America OnLine users, reveals its purpose is to track all web sites visited, including secure web pages for making purchases or financial transactions. Clicking on either ad for more information will inject the Alchem parasites directly into your computer which germinate into more parasites.
In order to find a browser that does not contain pests, you need to select one of the lesser known browsers for which no parasites exist. This means finding a browser that is a lot less popular or maybe does not contain all the multimedia functions you want. Or you can switch to Macintosh computers which occupy such a small percentage of the marketplace, that parasites have not yet been written for them. But if you stay with your current PC, then another choice is to download the Mozilla Firefox which does not contain parasites. In fact, your internet browsing will kick into high gear because there are no parasites slowing you down.
Quick Way to Detect Parasite Activity
Since many parasites are designed to start work when you go online, you may find some of them listed in a special configuration file on your computer. You can get to this Microsoft file by clicking on the “Start” button, then click “Run,” then type in “msconfig.exe” and click “OK.” Clicking on the “Startup” tab will open up a window you can scroll to see what programs were set to launch upon starting your computer. While most of these names are programs necessary to run your computer, the parasites, worms, trojans or viruses, if any, will be listed on the bottom of the list. You can verify them one at a time by typing their names in a search engine such as Google.
Items marked with a check are set to launch as soon as Windows opens up. Other items reside on your computer and will run if launched. The newest programs added to your computer are at the bottom of the list. This is likely where you will find parasites and their ilk. Start with the name on the bottom and type that file name in a search engine search box. When the search page opens with its list of selections, click on the “Cached” page to skim the titles until you find a web site page that mentions your file to see if it is a valid Windows file or not.
If you see parasites, adware, spyware, to anything similar, you should read that page by clicking on the “Cached” page to reduce your chance of acquiring new parasites by not going directly to any web site. This technique provides a useful introduction to where parasites reside on your computer. But it is only the first step in finding these pests. Chances are good that if you find one parasite listed, there are probably many more hiding on your computer.
As parasites become more sophisticated, many of them are now copying themselves onto legitimate systems files and folders that run your computer. Hewlett-Packard and America OnLine hide some of their snoopy programs in the Program Files directory using gentle names such as “Companion.” This can make detection more difficult and you may have to search for the parasite’s related files to determine if the file is the original or an infected variant.
Final Advice
You may receive e-mails offering to provide you with a free computer scan for viruses. Or, the e-mail may contain an alarming message that your user name or password has been compromised and you need to click on the link immediately or your account will be closed. Never click these links. They are never legitimate.
The blue hyperlinks lead to web sites with a false name or they spoof (fake) the name of a well-known web site, but which actually contain a parasite or trojan to steal your user name or password. Or, they may contain a redirect taking you to their scumware to sell illegal goods or services, or to snatch your account and password information before you have time to react with your mouse or keyboard.
Why do they want your identity? Sometimes for quick money to sell your personal information to identity thieves, and other times to shield their own identity in order to sell pornography, gambling, or illegal software on the internet. As soon as one stolen identity is uncovered, they slip into another person’s stolen identity and continue selling. Prosecuting these people is virtually impossible because they are located in other countries and international laws do not apply.
No Perfect Solutions
There are no perfect solutions. Firewalls are not designed to stop parasites and so they leap right into your computer. Anti-virus software will not block nor detect parasites. As long as legitimate companies use parasites for marketing tools, parasites will continue to thrive. For those of you inspired to remove parasites on your own, the popular Hijack This software program should help get you started.
The best way to avoid parasites is to keep your computer private if you can. Parasites spread through a home network, so unplug the children from the network. If your children must go online, use strict parental controls and restrictions set by you. Or plan to sit with them to see what they download for school projects, but do not let your children surf the internet from home. Send them back to school or the library for that purpose.
From now on, think of all gaming, music, video, software and animation web sites as potentially lethal traps to infect your computer with unwanted parasites. Gambling, pornographic and related web sites all contain parasites and many also carry trojans or worms related to credit card or identity theft.
Update: Since this article was uploaded August 6, 2004, internet spying has become an even bigger business. People who would never go to gambling or pornographic web sites, are now placing their identities in jeopardy by their greed for obtaining brand name software for free from these web sites.
The catch is they must agree to pay a one time fee of a few dollars on their credit card in order to have access to a promise of free, unlimited downloads of American software. But what they don’t realize is they are giving these crooks unlimited access to their credit card numbers and identity.
The old axiom of Buyer Beware is so true for the internet. Because the internet is worldwide, these illegal web sites operating in countries outside of your own are not covered by your legal system.
Skeptically yours,
Mim
 The 32-year-old D12 rapper was rushed to Holy Cross Hospital in a private vehicle after being shot once in the head and twice in the chest, but was pronounced dead on arrival on April 11, 2006. The second victim, 35-year-old Keith Bender, was on life support at St. John Conner Creek Hospital after being shot in the face by Proof but died a week later on April 18.
The 32-year-old D12 rapper was rushed to Holy Cross Hospital in a private vehicle after being shot once in the head and twice in the chest, but was pronounced dead on arrival on April 11, 2006. The second victim, 35-year-old Keith Bender, was on life support at St. John Conner Creek Hospital after being shot in the face by Proof but died a week later on April 18.

 An off-campus college party at 610 N. Buchanan Blvd. got out of control on March 13, 2006 when Lacrosse players at Duke University in Durham, North Carolina were accused of raping the black female stripper who was paid to be their evening entertainment. Not much information has been forthcoming from the other woman that came with her.
An off-campus college party at 610 N. Buchanan Blvd. got out of control on March 13, 2006 when Lacrosse players at Duke University in Durham, North Carolina were accused of raping the black female stripper who was paid to be their evening entertainment. Not much information has been forthcoming from the other woman that came with her. who is retired from the Navy and the National Guard, follows the military scene news and explains the Pat Tillman cover-up this way. Ed wrote: Here is the deal with with Pat Tillman the professional football player who was killed by friendly fire. He could have been killed by a bullet from his brother’s gun. His brother was fighting in the same group of fighters and his brother and the part of group he was in fired on the other American including his brother. They were reporting they were friendly and Americans but the commander kept the group firing.
who is retired from the Navy and the National Guard, follows the military scene news and explains the Pat Tillman cover-up this way. Ed wrote: Here is the deal with with Pat Tillman the professional football player who was killed by friendly fire. He could have been killed by a bullet from his brother’s gun. His brother was fighting in the same group of fighters and his brother and the part of group he was in fired on the other American including his brother. They were reporting they were friendly and Americans but the commander kept the group firing.







 Peeking into the programming code for this parasite customized for America OnLine users, reveals its purpose is to track all web sites visited, including secure web pages for making purchases or financial transactions. Clicking on either ad for more information will inject the Alchem parasites directly into your computer which germinate into more parasites.
Peeking into the programming code for this parasite customized for America OnLine users, reveals its purpose is to track all web sites visited, including secure web pages for making purchases or financial transactions. Clicking on either ad for more information will inject the Alchem parasites directly into your computer which germinate into more parasites.